二进制方式搭建Kubernetes 1.19.3高可用集群(一)——环境准备
发布时间:2020-11-01 21:14:44阅读:(533)
本文将通过二进制来搭建Kubernetes v1.19.3高可用集群,网络插件选择calico,kube-proxy使用ipvs模式
环境准备
centos7虚拟机11台,配置如下
| 系统类型 | IP | 角色 | Hostname |
| centos-7.7 | 10.0.40.101 | etcd | etcd-40-101.jieee.xyz |
| centos-7.7 | 10.0.40.102 | etcd | etcd-40-102.jieee.xyz |
| centos-7.7 | 10.0.40.103 | etcd | etcd-40-103.jieee.xyz |
| centos-7.7 | 10.0.50.101 | master | kube-m-50-101.jieee.xyz |
| centos-7.7 | 10.0.50.102 | master | kube-m-50-102.jieee.xyz |
| centos-7.7 | 10.0.50.103 | master | kube-m-50-103.jieee.xyz |
| centos-7.7 | 10.0.50.251 | haproxy | kube-ha-50-251.jieee.xyz |
| centos-7.7 | 10.0.50.252 | haproxy | kube-ha-50-252.jieee.xyz |
| centos-7.7 | 10.0.60.101 | worker | kube-n-60-101.jieee.xyz |
| centos-7.7 | 10.0.60.102 | worker | kube-n-60-102.jieee.xyz |
| centos-7.7 | 10.0.60.103 | worker | kube-n-60-103.jieee.xyz |
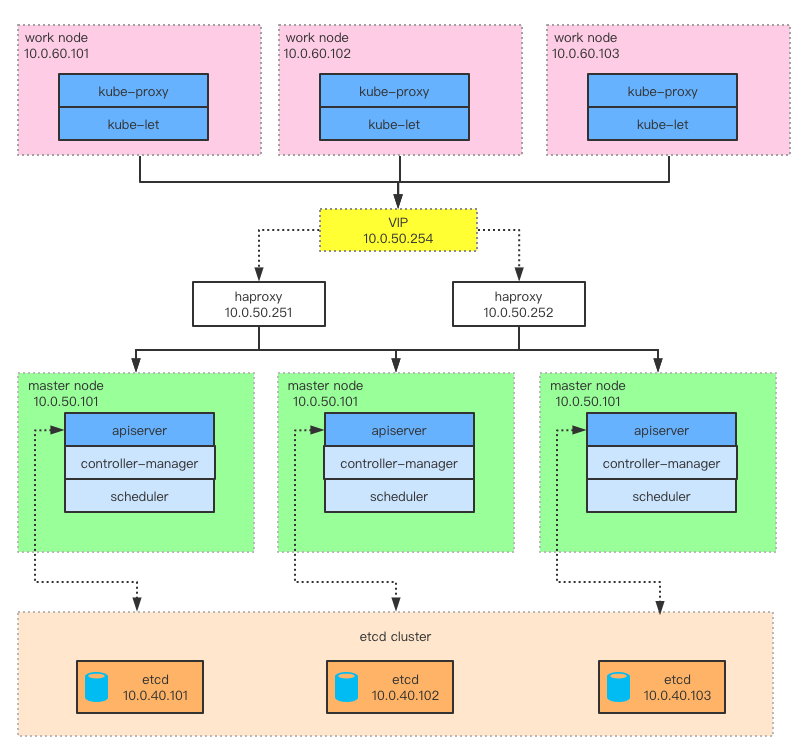
集群拓扑图
系统设置(master、worker节点上执行)
配置host
每个节点主机名必须不一样,并且要保证所有节点直接可以通过hostname相互访问
cat >> /etc/hosts <<EOF
10.0.50.101 kube-m-50-101.jieee.xyz
10.0.50.102 kube-m-50-102.jieee.xyz
10.0.50.103 kube-m-50-103.jieee.xyz
10.0.60.101 kube-n-60-101.jieee.xyz
10.0.60.102 kube-n-60-102.jieee.xyz
10.0.60.103 kube-n-60-103.jieee.xyz
EOF关闭firewalld,swap,Selinux,重置iptables
#关闭防火墙
systemctl stop firewalld
systemctl disable firewalld
#关闭swap
swapoff -a
sed -i '/swap/s/^\(.*\)$/#\1/g' /etc/fstab
#关闭selinux
setenforce 0
sed -i 's/enforcing/disabled/' /etc/selinux/config
#关闭dnsmasq
service dnsmasq stop
systemctl disable dnsmasq
#重置iptables
iptables -F && iptables -X && iptables -F -t nat && iptables -X -t nat && iptables -P FORWARD ACCEPT安装依赖软件
#更新yum
yum update
#安装依赖包
yum install -y ipset ipvsadm curl设置系统参数
#设置内核参数
cat > /etc/sysctl.d/k8s.conf<<EOF
net.ipv4.ip_forward = 1
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
vm.swappiness = 0
vm.overcommit_memory=1
vm.panic_on_oom=0
fs.inotify.max_user_watches=89100
EOF
#使配置文件生效
modprobe br_netfilter
sysctl -p /etc/sysctl.d/k8s.conf
#配置ipvs,保证系统重启后能自动加载ipvs模块
cat > /etc/sysconfig/modules/ipvs.modules<<EOF
#!/bin/bash
modprobe -- ip_vs
modprobe -- ip_vs_rr
modprobe -- ip_vs_wrr
modprobe -- ip_vs_sh
modprobe -- nf_conntrack_ipv4
EOF
chmod 755 /etc/sysconfig/modules/ipvs.modules
bash /etc/sysconfig/modules/ipvs.modules
lsmod | grep -e ip_vs -e nf_conntrack_ipv4安装docker(worker节点)
#如果存在旧的安装包,删除掉
yum remove -y docker* container-selinux
#安装必要的软件包
yum install -y yum-utils device-mapper-persistent-data lvm2
#添加yum源(这里使用了aliyun镜像加速)
yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
#安装docker(目前官方推荐安装19.03.11)
yum install docker-ce-19.03.11-3.el7 -y
#开机启动
systemctl enable docker
#配置docker镜像以及存储目录(我这里/data目录空间较大,所有把docker存储放在/data目录下)
mkdir -p /etc/docker
cat > /etc/docker/daemon.json<<EOF
{
"exec-opts": ["native.cgroupdriver=systemd"],
"registry-mirrors": ["http://hub-mirror.c.163.com"],
"graph": "/data/docker"
}
EOF
#启动docker
systemctl start docker准备二进制文件
配置免密登录
我们准备准备一台机器用于生产配置文件(可以是集群内的机器,也可以是非集群内的),为了方便复制文件,配置好此节点与集群内节点的免密登录
下载二进制文件
官方下载地址
k8s: https://github.com/kubernetes/kubernetes/releases
etcd: https://github.com/etcd-io/etcd/releases
网盘下载地址(我从官网下载整理好的文件)
链接: https://pan.baidu.com/s/1pQWsD0a9NOQgnTDqbaTYvg
密码: tbet
分发文件
#创建目录
ssh root@10.0.40.101 "mkdir -p /opt/kubernetes/bin"
ssh root@10.0.40.102 "mkdir -p /opt/kubernetes/bin"
ssh root@10.0.40.103 "mkdir -p /opt/kubernetes/bin"
ssh root@10.0.50.101 "mkdir -p /opt/kubernetes/bin"
ssh root@10.0.50.102 "mkdir -p /opt/kubernetes/bin"
ssh root@10.0.50.103 "mkdir -p /opt/kubernetes/bin"
ssh root@10.0.60.101 "mkdir -p /opt/kubernetes/bin"
ssh root@10.0.60.102 "mkdir -p /opt/kubernetes/bin"
ssh root@10.0.60.103 "mkdir -p /opt/kubernetes/bin"
#分发etcd文件
scp etcd/* root@10.0.40.101:/opt/kubernetes/bin
scp etcd/* root@10.0.40.102:/opt/kubernetes/bin
scp etcd/* root@10.0.40.103:/opt/kubernetes/bin
#分发master文件
scp master/* root@10.0.50.101:/opt/kubernetes/bin
scp master/* root@10.0.50.102:/opt/kubernetes/bin
scp master/* root@10.0.50.103:/opt/kubernetes/bin
#分发worker文件
scp worker/* root@10.0.60.101:/opt/kubernetes/bin
scp worker/* root@10.0.60.102:/opt/kubernetes/bin
scp worker/* root@10.0.60.103:/opt/kubernetes/bin创建配置文件
安装cfssl
wget "https://pkg.cfssl.org/R1.2/cfssl_linux-amd64" -O /usr/local/bin/cfssl
wget "https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64" -O /usr/local/bin/cfssljson
chmod +x /usr/local/bin/cfssl /usr/local/bin/cfssljson生成根证书
#所有证书都在target目录中生成,target目录可以随便放在哪儿
mkdir target && cd target
#创建ca-config.json
cat > ca-config.json<<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "87600h"
}
}
}
}
EOF
#创建ca-csr.json
cat > ca-csr.json<<EOF
{
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Hangzhou",
"L": "Hangzhou",
"O": "k8s",
"OU": "System"
}
]
}
EOF
#生成根证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca
#查看生成结果(最终需要的就是ca-key.pem和ca.pem)
ls ca*.pem
#ca-key.pem ca.pem分发根证书(分发至etcd、master、worker节点)
#创建证书存放目录
ssh root@10.0.40.101 "mkdir -p /etc/kubernetes/pki/"
ssh root@10.0.40.102 "mkdir -p /etc/kubernetes/pki/"
ssh root@10.0.40.103 "mkdir -p /etc/kubernetes/pki/"
ssh root@10.0.50.101 "mkdir -p /etc/kubernetes/pki/"
ssh root@10.0.50.102 "mkdir -p /etc/kubernetes/pki/"
ssh root@10.0.50.103 "mkdir -p /etc/kubernetes/pki/"
ssh root@10.0.60.101 "mkdir -p /etc/kubernetes/pki/"
ssh root@10.0.60.102 "mkdir -p /etc/kubernetes/pki/"
ssh root@10.0.60.103 "mkdir -p /etc/kubernetes/pki/"
#上传ca证书
scp ca*.pem root@10.0.40.101:/etc/kubernetes/pki/
scp ca*.pem root@10.0.40.102:/etc/kubernetes/pki/
scp ca*.pem root@10.0.40.103:/etc/kubernetes/pki/
scp ca*.pem root@10.0.50.101:/etc/kubernetes/pki/
scp ca*.pem root@10.0.50.102:/etc/kubernetes/pki/
scp ca*.pem root@10.0.50.103:/etc/kubernetes/pki/
scp ca*.pem root@10.0.60.101:/etc/kubernetes/pki/
scp ca*.pem root@10.0.60.102:/etc/kubernetes/pki/
scp ca*.pem root@10.0.60.103:/etc/kubernetes/pki/部分配置文件,详见GITEE
文章版权及转载声明:
文章转载或复制请以超链接形式并注明出处陌上小筑

发表评论